One of the difficult task today for the IT Pro is the escalation in depth to identify an authorization/authentication issue that comes randomly.
Logs and logs that should check and find the line or specific event log ID that probably cause the error.
You can find so many log management applications in the market and more intelligence applications that can do the task easier.
But sometimes the customer don't have the budget and must be do the escalation from every logs that has in different Servers/Workstations.
Recently undertake an authorization and authentication issue and start to escalate to find what cause the issue.
Unfortunately i had to read logs from Windows Event Log.
It wasn't exist and Log Management Application to do my task easier.
I realize that it's not exist any way to Filter the Event logs per user.
Here comes the Powershell to fill the gap and focus direct in the logs that you really need
I start to use the Get-EventLog but i found it that has been depreciated it and replace with the Get-WinEevnt.
So let's see how can filter out Windows Event Logs from Domain Controller by specific User.
Get-WinEvent has a property -Filterhashtable which can use it to specify a query in hashtable format to get the events that we want.
The query can contain a hash table with one or more key/values pair.
In the following table you can find out which are the valid key/pairs value that accept:
| Key Name | Value |
|---|---|
| LogName |
String[] |
| Provider Name | String[] |
| Path | String[] |
| Keywoards | Long[] |
| ID | Int-32[] |
| Level | Int-32[] |
| StartTime | Date-Time[] |
| EndTime | Date-Time[] |
| UserID | SID[] |
| Data | String[] |
| <named-data> | String[] |
Today we will use the UserID with the LogName in the example to filter Security Event Logs by specific User
So let's write down how to create our Powershell query.
- The UserID accept only SID so first of all we must found the SID of the specific user that want to filter out
- Type Get-ADUser -Identity <username>
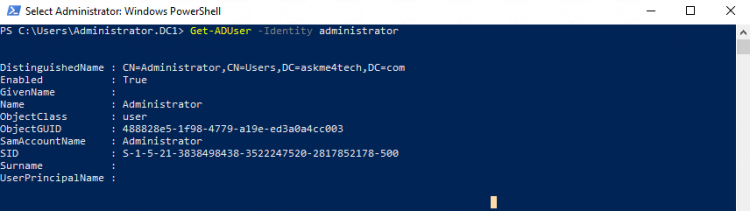
- The results will be like the following included the SID
- So here we go
- Type Get-WinEvent @{logname='security' ; userid='SID'}
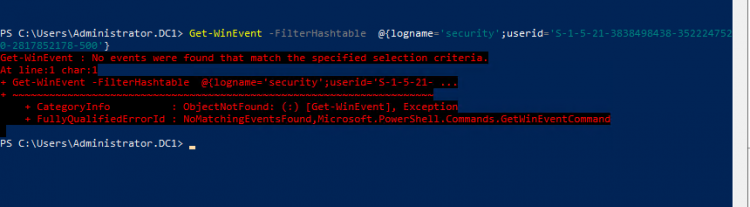
- What happened? I am sure that Security Logs exist for the specific user.
- Unfortunately the userid it's not working as expected in this scenario.
- But as alternative we can use the key data
- Type Get-WinEvent @{logname='security' ; data='SID'}
- Of course you can export the results in CSV or pipeline to Outgridview.
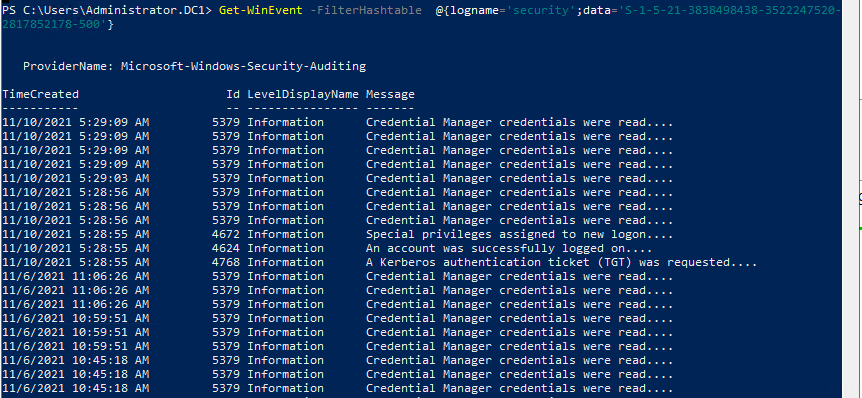
As you can see the Get-WinEvent can help us a lot and reduce the time to find out what exactly want from the Logs.







